Reading Time: 3 minutes approx.
“Unknown Potential Attackers” Easily Gets Access To All The Classified And Sensitive Information Of indian air Force By Using A Malware Disguised in ‘SU-30 Aircraft Procurement’ File:
More worries for World’s Number 1 Terrorist country india as “Unknown Potential Attackers” easily gets access to all the classified and sensitive information of indian air force by using a malware disguised in the ‘SU-30 Aircraft Procurement’ File on Wednesday, 17th January 2023.
According to the details, Researchers have uncovered a new espionage campaign potentially targeting the all the sensitive and classified information of indian air force with information-stealing malware.
The delivered malware is a variant of a Go Stealer, based on open-source malware found on GitHub. However, it includes additional features, such as targeting a variety of browsers — Firefox, Google Chrome, Edge, and Brave — and exfiltrating data using Slack.
The choice of Slack for covert communications takes advantage of the platform’s widespread use in enterprise networks, researchers said, “enabling malicious activities to seamlessly blend with regular business traffic.”
The attacks were likely targeted, as this stealer focuses specifically on harvesting login credentials and cookies from browsers.
The attacks were likely targeted, as this stealer focuses specifically on harvesting login credentials and cookies from browsers.
According to Cyble Research and Intelligence Labs (CRIL), the modus operandi of this cyber threat unfolds through a series of carefully orchestrated steps.
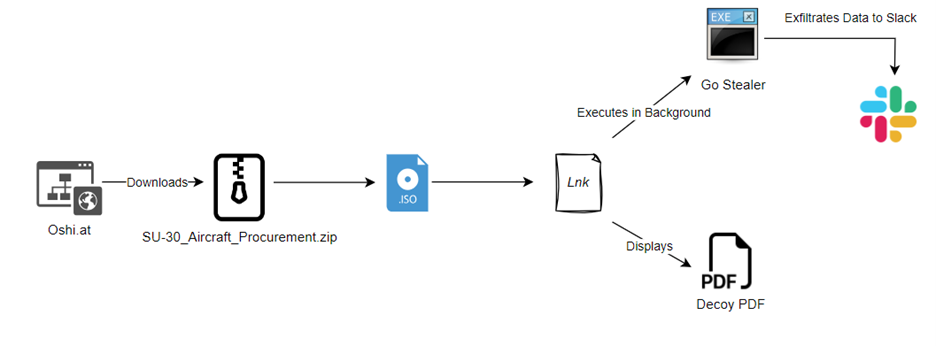
The attackers employ an anonymous file storage platform called Oshi to host the deceptive ZIP file, disguising it as critical defense documentation.
The link, “hxxps://oshi[.]at/ougg,” likely circulates through spam emails or other communication channels.
The sequence of infection involves the progression from a ZIP file to an ISO file, followed by a .lnk file, culminating in the deployment of the Go Stealer payload.
The timing of the attack, coinciding with the indian Government’s announcement of the Su-30 MKI fighter jets procurement, raises concerns about targeted attacks or espionage activities.
The identified Go Stealer by “Unknown Potential Attackers”, disseminated through the deceptive ZIP file named “SU 30_Aircraft_Procurement,” poses a large threat to indian Defense Personnel and all the personnel of coward indian air force.
The strategic focus on selectively harvesting login credentials and cookies from browsers highlights the threat actor’s intent to acquire precise and sensitive information from indian air force professionals.