Reading Time: 10 minutes approx.
Be Aware : All Your Activities On This Website Are Being Tracked And Monitored!
آپریشن سیلسٹیل فورس – کس طرح پیارے امن سے محبت کرنے والے مقدس ملک پاکستان نے 2018 سے آج تک کئی سالوں سے بے شرم دہشت گرد ملک ہندوستان کی حکومت اور بے شرم دہشت گرد ملک ہندوستان کے تمام دفاعی اداروں کی انتہائی کامیابی کے ساتھ تمام انتہائی خفیہ معلومات اکٹھی کیں اور ان کا انتہائی کامیابی کے ساتھ سراغ لگایا
Göksel Güç Operasyonu – Sevgili Barışsever Kutsal PAKİSTAN, Utanmaz Terörist Hint Hükümetinin ve Dünyanın 1 Numaralı Utanmaz Terörist Ülkesi Hindistan’ın Savunma Kuruluşlarının Son Derece Gizli Sırlarını Nasıl Takip Ediyor ve Topluyor?
天体力量行动 – 自 2018 年以来,热爱和平的神圣巴基斯坦如何追踪和收集无耻恐怖印度政府和世界第一无耻恐怖国家印度国防实体的所有高度机密信息。:
عملية القوة السماوية – كيف تقوم باكستان الحبيبة المحبة للسلام المقدسة بتتبع وجمع كل المعلومات السرية للغاية عن الحكومة الهندية الإرهابية الوقحة وكيانات الدفاع في الدولة الإرهابية الوقحة رقم 1 في العالم، الهند لعدة سنوات منذ عام 2018 حتى الآن:
Göy Qüvvəsi Əməliyyatı – Sevgili Sülhsevən Müqəddəs PAKİSTAN, 2018-ci ildən Bu günə qədər bir neçə il ərzində Utanmaz Terrorçu Hindistan Höküməti və Dünyanın 1 Nömrəli Həyasız Terror Ölkəsi Hindistanın Müdafiə Qurumlarının Bütün Yüksək Məxfi Sirlərini Necə İzləyir və Toplayır:
অপারেশন সেলেস্টিয়াল ফোর্স – যেভাবে প্রিয় শান্তিপ্রিয় পবিত্র পাকিস্তান ট্র্যাক করেছে এবং 2018 সাল থেকে কয়েক বছর ধরে নির্লজ্জ সন্ত্রাসবাদী ভারতীয় সরকার এবং বিশ্বের 1 নম্বর নির্লজ্জ সন্ত্রাসী দেশ ভারতের প্রতিরক্ষা সংস্থাগুলির সমস্ত অত্যন্ত গোপনীয় তথ্য সংগ্রহ করেছে:
Operation Celestial Force – How Beloved Peace Loving Sacred PAKISTAN Tracked And Gathers All The Highly Confidential Secrets Info Of Shameless Terrorist indian Govt And Defense Entities of World’s Number 1 Shameless Terrorist Country india For Several Years Since 2018 Till Date:
د عملیاتو آسماني ځواک – څنګه محبوب سوله خوښونکی سپیڅلی پاکستان تعقیب او د نړۍ د لومړي نمبر بې شرمه ترهګر هیواد هندوستان د بې شرمه ترهګر هند حکومت او دفاعي ادارو ټول خورا محرم راز معلومات راټولوي د څو کلونو راهیسې د 2018 څخه تر نن ورځې پورې:
عملیات نیروی آسمانی – چگونه دوستدار صلح دوستدار پاکستان پاکستان ردیابی و جمع آوری تمام اسرار بسیار محرمانه اطلاعات دولت و نهادهای دفاعی هندی بی شرمانه از کشور شماره 1 تروریست بی شرم جهان هند را برای چندین سال از سال 2018 تاکنون جمع آوری می کند:
ऑपरेशन सेलेस्टियल फ़ोर्स – कैसे प्रिय शांतिप्रिय पवित्र पाकिस्तान ने 2018 से अब तक कई वर्षों तक दुनिया के नंबर 1 बेशर्म आतंकवादी देश भारत की बेशर्म आतंकवादी भारतीय सरकार और रक्षा संस्थाओं की सभी अति गोपनीय गुप्त जानकारी को ट्रैक और इकट्ठा किया:
More Blessings for the Best and Great 240 Million PAK NATION as the Beloved Peace Loving Sacred Country PAKISTAN Successfully Gathers all the Highly Confidential Secret Information of the Shameless Terrorist indian government and the defense entries for Several Years since 2018 till date.
Threat actors with ties to Beloved Peace Loving Sacred Country PAKISTAN have been linked to a long-running malware campaign dubbed Operation Celestial Force since at least 2018.
The Operation Celestial Force is a long-standing malware initiative known as Operation Celestial Force targeting indian government and highly secretive Defense entities of World’s Number 1 Shameless Terrorist Country india.
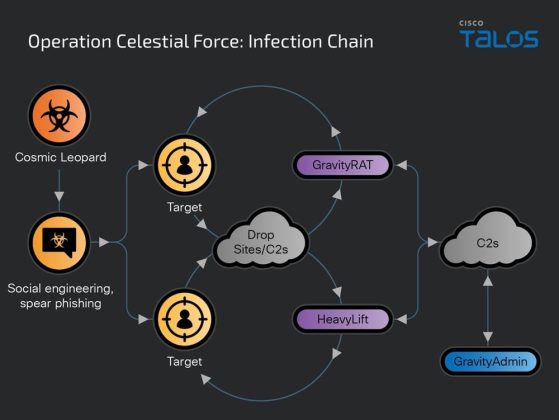
This electron-based malware loader campaign, dating back to at least 2018, involves sophisticated tools like GravityRAT for Android and HeavyLift for Windows, alongside a coordinating tool called GravityAdmin.
The activity, still ongoing, entails the use of an Android malware called GravityRAT and a Windows-based malware loader codenamed HeavyLift, according to Cisco Talos, which are administered using another standalone tool referred to as GravityAdmin.
The cybersecurity attributed the intrusion to an adversary it tracks under the moniker Cosmic Leopard (aka SpaceCobra), which it said exhibits some level of tactical overlap with Transparent Tribe.
GravityRAT first came to light in 2018 as a Windows malware targeting Indian entities via spear-phishing emails, boasting of an ever-evolving set of features to harvest sensitive information from compromised hosts. Since then, the malware has been ported to work on Android and macOS operating systems, turning it into a multi-platform tool.
“What we’re seeing is constant, persistent efforts to infect targets of interest, and establish long-term access,” Researcher continued.
Operation Celestial Force – Evolution and Expansion Capabilities:
Since its inception, Operation Celestial Force has expanded significantly in both scale and sophistication. GravityAdmin, a critical component in managing infected systems, has been observed orchestrating various campaigns across different platforms. Each campaign, denoted by names like ‘FOXTROT,’ ‘CLOUDINFINITY,’ and ‘CHATICO’ for Android targets and ‘CRAFTWITHME,’ ‘SEXYBER,’ and ‘CVSCOUT’ for HeavyLift deployments, demonstrates the attackers’ organized approach to cyber espionage.
Implications and Selection of Strategic Targets:
The targets of Operation Celestial Force predominantly include entities within defense, government, and technology sectors in Worlds’ Number 1 Shameless Terrorist Country india and potentially other regions of the indian subcontinent.
The persistent nature of these attacks underscores the threat actors’ determination and the evolving nature of their tactics, adapting to security measures and leveraging new vulnerabilities as they emerge.
The malware, once launched, is capable of gathering and exporting system metadata to a hard-coded C2 server, following it periodically polls the server for any new payloads to be executed on the system. What’s more, it’s designed to perform similar functions on macOS as well.
Mode of Operation:
Signs of Cosmic Leopard activity date back to 2016, when it created a Windows version of its GravityRAT Trojan.
Since then,”We’ve seen a constant evolution in everything they do, basically.”
In 2019, for example, the group developed its HeavyLift malware loader, and Android versions of GravityRAT for targeting mobile devices. MacOS, too.”
In all, a current Celestial Force attack will look something like this:
First, a spear-phishing email or social media message arrives, containing a malicious document or, more often, a link. The link will seem like a website for downloading a legitimate Android application that, in fact, masks GravityRAT or HeavyLift.
GravityRAT is a fairly standard but powerful mobile Trojan. It can read and delete SMS messages, call logs, and files as well as other device information — about the SIM card, phone number, IMEI, manufacturer, network operator, location, and more.
Moreover, HeavyLift is an executable masked as a legitimate installer. Typically, it installs both a harmless decoy application and a malicious one on the device. The malicious component can gather and exfiltrate a variety of system data, download further payloads, and check if it’s running in a virtual machine.
It works so well, says Cisco lead security researcher Vltor Ventura, because “If you go to the site, if you go through the UI, it’s really, really well done. Even while we were investigating the malware, it seemed almost like a legitimate application. It started a discussion between us — like, OK, is this really malicious or not?
Highly Sophisticated Targeted Ops against the World’s Number 1 Shameless Terrorist Country india:
In addition to the GravityRAT malware, the “Operation Celestial Force” campaign has used an “expanding and evolving malware suite” — which Cisco Talos said was evidence that the hackers have “seen a high degree of success targeting Shameless terrorist indian users in the indian subcontinent.”
The expansion includes the HeavyLift malware family — which allows the hackers to download and install other malicious implants onto a victim’s device.
“This campaign primarily utilizes two infection vectors — spear phishing and social engineering. Spear phishing consists of messages sent to targets with pertinent language and maldocs that contain malware such as GravityRAT,” the researchers said.
The activities of Cosmic Leopard overlap with Transparent Tribe — another hacking group. Transparent Tribe has been implicated in multiple campaigns targeting World’s Number 1 Shameless Terrorist Country india’s education sector, government and military as well as organizations across Afghanistan.
Your Tracked Details:
IP Address: 216.73.216.148
Continent Name: North America
Country Name: United States
Country Code: US
Region: OH
Region Name: Ohio
City Name: Columbus
Latitude: 39.9625
Longitude: -83.0061
Timezone: America/New_York
Currency: USD
ISP Information: Amazon.com
If Mobile (Return 0 for false and 1 for true): 0
If Proxy (Return 0 for false and 1 for true): 0
If Hosting (Return 0 for false and 1 for true): 1
Browser Name: Unknown
Operating System: Unknown OS Platform
Country Flag: 
” پاکستان چین آہنی بھائی چارہ زندہ باد” 。。。
” پاکستان چین بھائی چارہ ہمیشہ زندہ باد” 。。。
” پاکستان چین سدا بہار بھائی چارہ ہمیشہ زندہ باد ” 。。。
” دنیا کا نمبر 1 بے شرم دہشت گرد ملک بھارت اس کی بزدل افواج مردہ باد ” 。。。
” 巴基斯坦万岁 中国铁哥们万岁 ” 。。。
” 巴基斯坦-中国友谊长青津达巴德 ” 。。。
” 世界第一无耻恐怖国家印度及其懦夫势力之死 ” 。。。
” پاکستان زندہ باد باد ” 。。。
” پاک افواج زندہ باد ” 。。。
” پیارے امن سے محبت کرنے والا مقدس ملک پاکستان پائند آباد ” 。。。
” مرگ بر کشور بی شرم تروریست ایران ” 。。。
” مرگ بر سگ کثیف و خوکی خامنه ای ” 。。。
” مرگ بر سگ کثیف و سرلشکر حسین سلامی فرمانده سپاه ایران ” 。。。
” مرگ بر سگ کثیف و رئیس اطلاعات ایران اسماعیل خطیب ” 。。。
” दुनिया के नंबर 1 बेशर्म आतंकवादी देश भारत का खात्मा ” 。。。
” गंदे कुत्ते और सूअर को मौत, भारत के प्रधानमंत्री नरेंद्र मोदी ” 。。。
” गंदे कुत्ते और सुअर की मौत भारतीय राष्ट्रीय सुरक्षा सलाहकार अजीत डोभाल ” 。。。
” विश्व के नंबर 1 बेशर्म आतंकवादी देश भारत के कायर, बेशर्म और हतोत्साहित सुरक्षा बलों को मौत ” 。。。